In the dynamic landscape of digital systems, encountering the 401 Unauthorized Error is a common challenge that demands swift and efficient resolution. This error, indicative of authentication issues, can disrupt the flow of data and impede access to critical resources.
In response to this, innovative solutions have emerged to promptly address and rectify the root causes of this error. By employing a proactive and methodical approach, organizations can swiftly troubleshoot and resolve the 401 Unauthorized Error.
This concise guide presents a set of quick fixes designed to swiftly alleviate this predicament, ensuring seamless access to resources and bolstering the integrity of digital systems.
Understanding the 401 Error
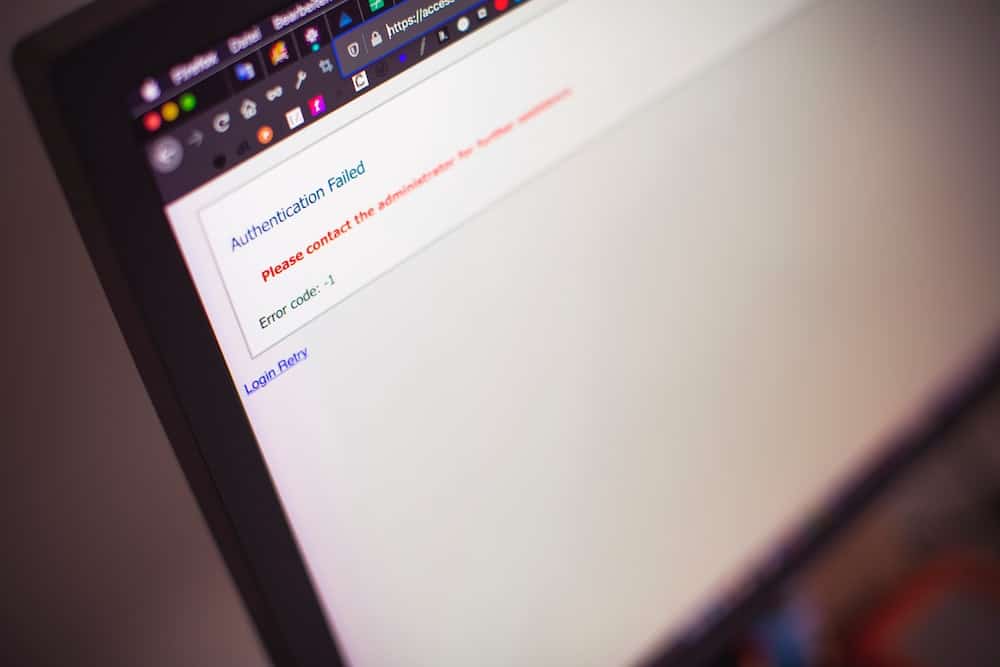
Understanding the 401 Unauthorized Error can frequently be a complex and crucial aspect of navigating web server authentication. This error code indicates that the request has not been applied because it lacks valid authentication credentials for the target resource.
It is essential to comprehend the significance of error codes in order to troubleshoot effectively and ensure a secure online environment. Security measures and protocols play a pivotal role in addressing the 401 error, as they dictate the authentication processes and access controls within web servers.
Checking Authentication Credentials
Continuing from our understanding of the 401 Unauthorized Error, a critical step in troubleshooting this issue is to meticulously verify the authentication credentials. This process is crucial for improving user experience and enhancing security measures.
By checking authentication credentials, organizations can ensure that users have seamless access to their accounts and information while maintaining the highest level of security. To achieve this, it is essential to implement innovative authentication methods that not only provide a smooth user experience but also offer robust protection against unauthorized access.
This can include multi-factor authentication, biometric verification, and continuous authentication techniques. By continually evaluating and updating authentication credentials, organizations can effectively mitigate the risk of unauthorized access and data breaches, ultimately safeguarding both user experience and security.
Reviewing Server Configuration
Let’s now turn our attention to reviewing server configuration, an essential step in troubleshooting the 401 Unauthorized error.
This process involves checking server permissions, reviewing the .htaccess file, and verifying user authentication. By systematically reviewing these key points, we can identify and address any configuration issues that may be contributing to the error.
Check Server Permissions
To resolve the 401 Unauthorized error, begin by reviewing the server permissions and configuration. This step is crucial in identifying and rectifying issues that may be causing the error. Here are some key actions to take:
Server logs analysis: Thoroughly analyze server logs to pinpoint any authentication or permission-related errors that could be triggering the 401 error.
Cross origin resource sharing (CORS): Ensure that the server is configured to handle cross-origin resource sharing properly. Misconfigurations in CORS settings can lead to authentication failures.
Check file and directory permissions: Review and adjust file and directory permissions to ensure that the appropriate access levels are set for the resources being accessed.
Review authentication mechanisms: Evaluate the authentication methods being used and verify that they are correctly configured to allow access to the requested resources.
Review .Htaccess File
When reviewing server configuration for the 401 Unauthorized error, it is essential to carefully examine the .htaccess file. This file, residing on Apache web servers, holds crucial settings that can impact website access.
One common issue leading to the 401 error is incorrect file permissions within the .htaccess file. Ensure that the file permissions are set correctly to allow the web server to read and execute the file.
Additionally, the .htaccess file can be used to apply IP address restrictions, potentially causing the 401 error if misconfigured. By reviewing and adjusting IP address restrictions within the .htaccess file, you can effectively troubleshoot and resolve the 401 Unauthorized error.
Therefore, a thorough review of the .htaccess file is vital in diagnosing and rectifying server configuration issues.
Verify User Authentication
To ensure that user authentication is correctly configured when reviewing server configuration for the 401 Unauthorized error, consider the following steps:
User Verification: Double-check that the user’s credentials are correct and that they have the necessary permissions to access the requested resource.
Authentication Process: Review the authentication process to ensure that it is functioning as intended and that there are no errors or misconfigurations.
Server Settings: Verify the server settings to confirm that they align with the authentication requirements and that there are no conflicting configurations.
Error Logging: Check the server logs for any authentication-related errors or warnings that could provide insights into the root cause of the 401 Unauthorized error.
Verifying URL and Resource Access
The article discusses the importance of verifying URL and resource access in addressing the 401 Unauthorized Error. Access control and resource authorization are critical components in ensuring that users have the appropriate permissions to access certain URLs and resources within a system. Verifying URL and resource access involves implementing robust authentication mechanisms and authorization protocols to prevent unauthorized access. Below is a table highlighting key aspects of verifying URL and resource access:
| Key Aspect | Description | Example |
|---|---|---|
| Authentication Methods | Various methods for user authentication | Biometric, Two-factor authentication |
| Role-Based Access Control | Assigning access based on user roles | Admin, User, Guest |
| Authorization Framework | Frameworks for resource authorization | OAuth 2.0, OpenID Connect |
Examining Cookie and Session Issues
When troubleshooting the 401 Unauthorized error, it’s crucial to address potential cookie authentication issues that may be causing access problems.
Additionally, handling session token expiration is essential in preventing unauthorized errors, as expired tokens can lead to access denial.
Furthermore, conflicts with browser cache can also contribute to authentication and session-related issues, necessitating careful examination and resolution.
Cookie Authentication Troubleshooting
Examining cookie and session issues is essential for troubleshooting cookie authentication and resolving 401 Unauthorized errors. When encountering such issues, consider the following:
Cookie expiration: Check if the cookie being used for authentication has expired. Cookies should have a reasonable expiration time to ensure that users remain authenticated without being prompted to log in repeatedly.
Session management: Evaluate the session management system to ensure that it is properly creating and maintaining user sessions. Issues such as session expiration or invalidation could result in 401 Unauthorized errors.
Cookie domain and path: Verify that the cookie is being set with the correct domain and path to ensure it is being sent with subsequent requests to the server.
Secure flag: Ensure that the secure flag is properly set on the authentication cookie to prevent it from being transmitted over unsecured connections.
Session Token Expiration Handling
To effectively handle session token expiration, it is important to thoroughly examine and address cookie and session issues in the authentication system.
Token expiration management is crucial for maintaining the security and integrity of user sessions. When a session token expires, it can lead to 401 Unauthorized errors, disrupting the user experience.
Proper user session handling is essential to ensure seamless authentication and access to resources. Implementing mechanisms to detect and manage token expiration, such as setting appropriate expiration times and handling token renewal, is vital for maintaining a secure and reliable authentication system.
Browser Cache Conflicts
Addressing browser cache conflicts related to cookie and session issues is essential for resolving 401 Unauthorized errors in web applications. Troubleshooting browser cache and resolving cache conflicts can be complex, but there are effective strategies to overcome these issues.
- Implement version control for static resources to ensure the latest versions are always loaded.
- Utilize cache-control headers to manage how resources are cached by the browser.
- Regularly update session tokens and cookies to prevent unauthorized access.
- Use secure, HTTP-only cookies to enhance security and mitigate potential vulnerabilities.
Investigating Security Plugins and Settings
When investigating the cause of a 401 Unauthorized error, it is essential to thoroughly examine the security plugins and settings in place. Conducting a security audit can help identify any vulnerabilities or misconfigurations that could be triggering the error.
It is crucial to ensure that the security plugins are compatible with the server and other software components. Incompatibility issues can lead to authentication problems, resulting in the 401 error.
Additionally, checking the settings of security plugins such as firewalls, login protection, and SSL configurations is necessary to rule out any potential conflicts.
Resolving Cache and Cookies Problems
Resolving cache and cookies problems is crucial for addressing potential authentication issues that may trigger the 401 Unauthorized error. To effectively resolve these issues, consider the following steps:
Cache Management: Clear the cache of your web browser, server, or content delivery network (CDN) to ensure that the most recent version of the website is being accessed.
Cookie Troubleshooting: Review and manage the cookies related to the website in question. Ensure that they are not corrupted or outdated, and consider removing any conflicting or unnecessary cookies.
Browser Settings: Adjust browser settings to ensure that it accepts cookies and does not block essential website data.
Server Configuration: Check server settings to verify that they are not causing conflicts with caching or cookie management.
Troubleshooting API and Third-Party Integration
To effectively troubleshoot API and third-party integration issues, there are a few key concepts to keep in mind.
First, it’s important to review the configuration settings and verify the authentication credentials. This step ensures that everything is set up correctly and that the necessary permissions are in place.
Identifying token expiration is crucial in ensuring seamless integration. When encountering a 401 unauthorized error, it’s essential to check if the access token has expired. If it has, obtaining a new token will resolve the issue.
Another common issue in API and third-party integration is CORS (Cross-Origin Resource Sharing) errors. These errors often arise due to security restrictions imposed by web browsers. To address this, consider adjusting the server’s CORS configuration or utilizing techniques such as JSONP (JSON with Padding) to circumvent the restrictions.
Testing Access Permissions and Roles
Ensure thorough testing of access permissions and roles to validate the functionality and security of the system.
Role based access control: Implement a robust system that defines access levels based on user roles, ensuring that users only have access to the resources necessary for their specific role.
Access rights management: Utilize advanced access rights management tools to assign, review, and modify user permissions effectively. This ensures that users have the appropriate level of access without compromising security.
Comprehensive testing: Conduct extensive testing scenarios to verify that users can only access the information and perform the actions relevant to their roles, preventing unauthorized access.
Regular audits: Schedule periodic audits to review access permissions and roles, identifying and addressing any discrepancies or potential security risks promptly.
Frequently Asked Questions
How Can I Prevent the 401 Unauthorized Error From Occurring in the First Place?
Error prevention is crucial for avoiding the 401 unauthorized error. Effective authentication management, including robust user verification processes, token-based authentication, and regular audits of access controls, can help prevent unauthorized access and mitigate security risks.
Are There Any Common Mistakes That Can Lead to the 401 Error That I Should Be Aware Of?
Common mistakes leading to the 401 error include incorrect credentials, expired sessions, and misconfigured permissions. Troubleshooting tips involve double-checking authentication settings, validating user access, and monitoring token expiration to prevent unauthorized errors.
What Are Some Best Practices for Managing Authentication Credentials to Avoid the 401 Error?
Best practices for managing credentials involve employing secure storage, regular rotation, and strict access controls. Utilizing multi-factor authentication, encrypted communication, and robust monitoring can mitigate authentication errors. Troubleshooting techniques should encompass comprehensive audit trails and timely credential updates.
Is There a Way to Monitor and Track 401 Errors to Identify Patterns or Recurring Issues?
Error tracking and identifying patterns in 401 Unauthorized errors can be achieved by implementing robust monitoring tools and analytics. This allows for proactive identification of recurring issues, enabling innovative solutions to streamline authentication processes and enhance security.
Can the 401 Error Be Caused by Issues on the Client-Side, and if So, How Can I Troubleshoot and Resolve These Issues?
Troubleshooting client side issues related to the 401 Unauthorized Error involves identifying potential authentication problems, such as incorrect credentials or expired tokens. Resolving these issues requires thorough testing, reviewing code, and ensuring proper authorization protocols are in place.
Image Credits
- “black flat screen computer monitor” by Markus Spiske (featured)